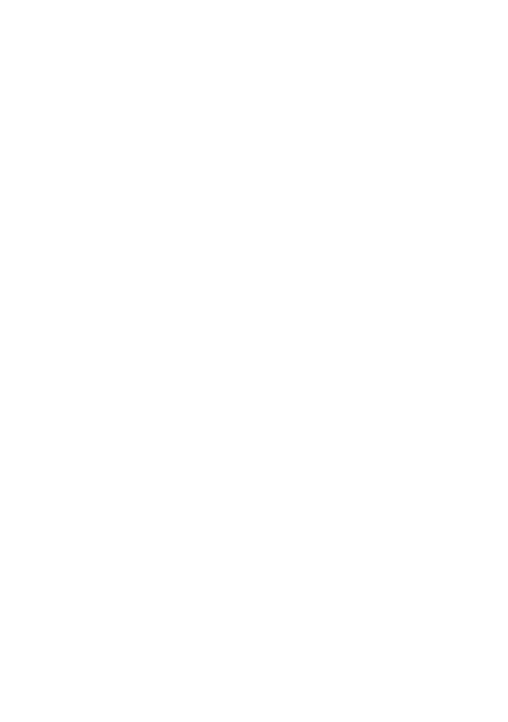Crypto Scams: Hacking Campaigns Compromise Coinbase Accounts
Crypto Hackers Steal Billions Yearly
The victims of cryptocurrency scams and crypto hacking represent a loss of nearly $2 billion in 2023, according to cryptosecurity firm CertiK. Big news stories such as the Ledgers Library leak and the KyberSwap hack represent common threats to the cryptocurrency and Web3 world. Sophisticated threat actors often carry out these attacks with the knowledge, capabilities, and motivation to drain wallets of thousands and sometimes millions of dollars in crypto assets, with the most popular target cryptocurrencies being Bitcoin and Ethereum. Many of these big crypto-hacking stories affect the big fish in the cryptocurrency world, such as crypto exchanges, Web3 technology stacks, a specific blockchain, and digital crypto wallets. However, how do malicious hackers or scammers scam everyday people into giving up their account information? What tricks and technologies do they use? This blog post will explore a real-world example of a crypto phishing campaign designed to scam Coinbase account holders in order to steal crypto.
Crypto Wallets: What is Coinbase?
Coinbase, a leading digital currency exchange in the United States, was founded in 2012. With its annual revenue in the billions of dollars, Coinbase has become the largest cryptocurrency exchange in the US by volume. Coinbase provides users with a platform to buy, sell, and exchange a vast range of cryptocurrencies, making it a go-to destination for crypto traders and investors. As one of the most widely used cryptocurrency exchanges, Coinbase, and its account holders are susceptible to cyber-attacks and other malicious activities by cyber criminals and hackers, particularly phishing attacks.
What is Phishing?
Phishing is a technique used by hackers, cybercriminals, and other malicious actors to gain access to personal information and accounts. The term "phishing" is derived from "fishing", where fishers use bait to catch fish. Similarly, cybercriminals use bait to lure victims into opening malicious emails and texts, which can lead to various types of cyber-attacks.
Phishing: A Persistent Threat to Your Crypto Account
Cryptocurrency scams in the form of phishing attacks are a widespread and significant threat to people who use digital wallets like Coinbase and Exodus. These attacks are designed to deceive users into divulging personal information through counterfeit login pages for cryptocurrency exchanges. The ultimate goal of these attacks is to steal sensitive user information, such as login credentials. Cryptocurrency accounts without two-factor or other forms of multifactor authentication are particularly susceptible to these attacks. Attackers can also use phishing tactics to trick users into downloading and installing harmful software or malware that can be used to drain cryptocurrency wallets. Therefore, it's crucial to be vigilant and take appropriate measures to safeguard personal information and digital assets from these types of attacks.
Figure 1 - A Coinbase-themed phishing email
Phishing emails contain a psychological component or trigger and are engineered for their target audience or individual; this is called social engineering. Psychological triggers deployed in phishing attacks can include fear, confidence, stress, authority, or greed. Often, financially motivated scammers and hackers use fear, stress, greed, and psychological pressure to entice victims to click on malicious links. The victims often click on impulse based on these psychological triggers without first analyzing the phishing email to ensure its authenticity. In the case of Figure 1, the cybercriminals are also using the authority fallacy to add credibility to the phishing email by using a domain that appears to come from a domain that deals with security.
Figure 2 - Source code snippet of a Coinbase phishing email pointing to Google Drive
Most of these phishing emails I've uncovered point to an external PDF document hosted on Google Drive as a shared document. In fact, this is such a popular phishing technique using Google Drive that I created a YARA rule specifically to hunt down these emails on VirusTotal. Many of these phishing emails use Google Drive to steal sensitive information, such as usernames and passwords, from cryptocurrency exchanges and wallets and popular banks, such as Wells Fargo, Bank of America, and Chase Bank. Even though it's popular to use Google Drive to host these malicious phishing documents, attackers can host them on other cloud storage applications like Dropbox or Microsoft OneDrive.
Figure 3 - Collection of Google Drive Phishing Emails collected from VirusTotal
The scammers attempt to entice the victim into opening this malicious document on your machine, where they can use psychological triggers or lures to generate further actions from the victim, leading to further system compromise or compromising the victim's crypto account or cryptocurrency wallet. As seen above, many phishing emails use lures such as "Your account has been locked", "Fraud found on your account”, and "Unrecognized login detected". These psychological triggers pressure potential phishing victims into making rash decisions to click on malicious links by creating stress and insinuating that the integrity of the account is in jeopardy.
Figure 4 - A malicious PDF document with a button that links attached to an attacker-controlled domain
Analyzing a Malicious Cryptocurrency-themed PDF
These malicious PDF documents are sent directly to the victim as an email attachment or a link to a cloud-hosted document. In this example, a malicious email contains a malicious link to a PDF hosted on Google Drive; this phishing technique relies on the phishing victim opening the email, then opening the document through the email, and then opening the link inside the shared PDF itself. We can explore the links embedded inside this malicious PDF using tools such as pdf-parser.py or plain using built-in tools like sed and grep. We'll use pdf-parser to find the PDF object responsible for handling the button action link of the malicious PDF file.
Figure 5 -The PDF obj contains the malicious link when the "Verify Account Information" button is pressed.
Upon inspecting and analyzing the embedded link inside the PDF action to a URL object, we can deduce that the URL hxxps[://]lineadditionalconnection[.]page[.]link/jTpt?oekdagew is a Dynamic Link based on the page.link content of the page, Dynamic links are a part of the Google Firebase service. You may be wondering what Google Firebase is. Well Google Firebase is a comprehensive mobile and web application development platform that offers a variety of tools and services to help developers build, improve, and scale their applications more easily. One feature within Firebase is called Dynamic Links; these intelligent links allow developers to create links across different platforms and devices. These intelligent links can adapt to the user's platform and lead to different destinations based on the user's device, operating system, or whether the app is installed. Tools such as Dynamic Links ensure a seamless and personalized user experience regardless of the platform or device a user engages on.
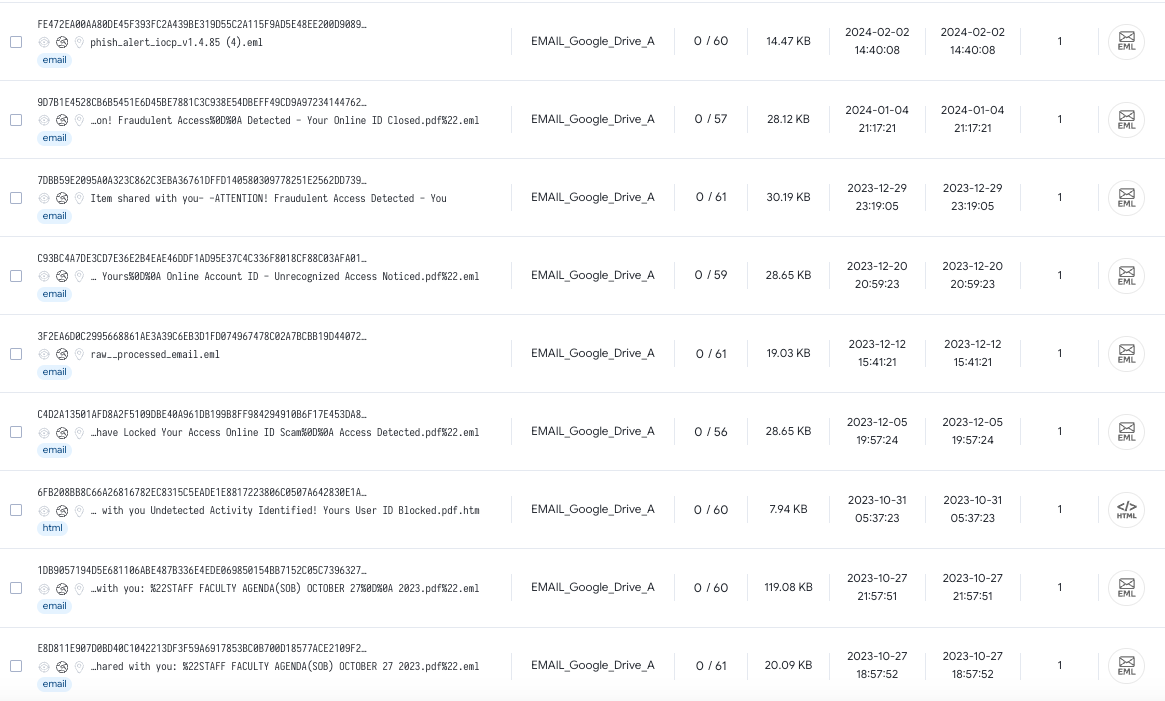
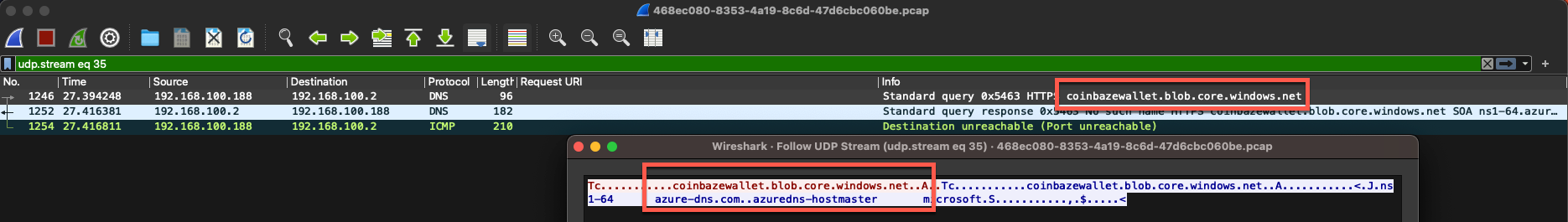
Analyzing this malicious PDF through a sandbox, we can see that the Google Firebase Dynamic Link reaches out to another URL. This URL, coinbazewallet[.]blob[.]core[.]windows[.]net is hosted on Microsoft Azure Blob storage. As of writing this blog, the malicious Azure blob storage has been taken down, but many similar ones have popped up as attackers devise new ways to scam cryptocurrency holders.
Figure 6 - Network traffic showing DNS request to Microsoft Blob Storage
In another phishing sample, we see the resultant capture page designed to spoof the legitimate Coinbase login portal.
Cloning the Coinbase.com Login Page
In the Coinbase crypto scam campaign, I uncovered the attackers cloned the Coinbase.com login page to entice Coinbase users into logging into a fake portal to steal Coinbase account usernames and passwords. Phishing tools such as GoClone can be used to fully clone a website's structure and assets in order to be used in phishing campaigns; this is a very popular technique for attackers looking to steal user credentials. Besides theft, stolen credentials can be used to compromise organizations further, such as ransomware attacks, as many businesses rely on services such as Microsoft Office 365.
Figure 7 - Side-by-Side between Coinbase Portal & Phishing Portal
By comparing the legitimate Coinbase login page with a cloned version, one can easily see how these types of crypto scams can easily deceive users. The differences between the two sites become apparent when examining their URLs. The login page on the left is from Coinbase.com, which uses SSL/TLS to provide secure access. On the other hand, the image on the right depicts a login page from the coinbasce-crypto[.]com domain, cunningly crafted to trick unsuspecting victims with a similar name. Beyond this, the fake Coinbase login page lacks a valid TLS certificate and is marked with a warning symbol, indicating an insecure web connection. As a result, users should exercise caution when presented with such pages, as they may be fraudulent and put their personal and financial information at risk.
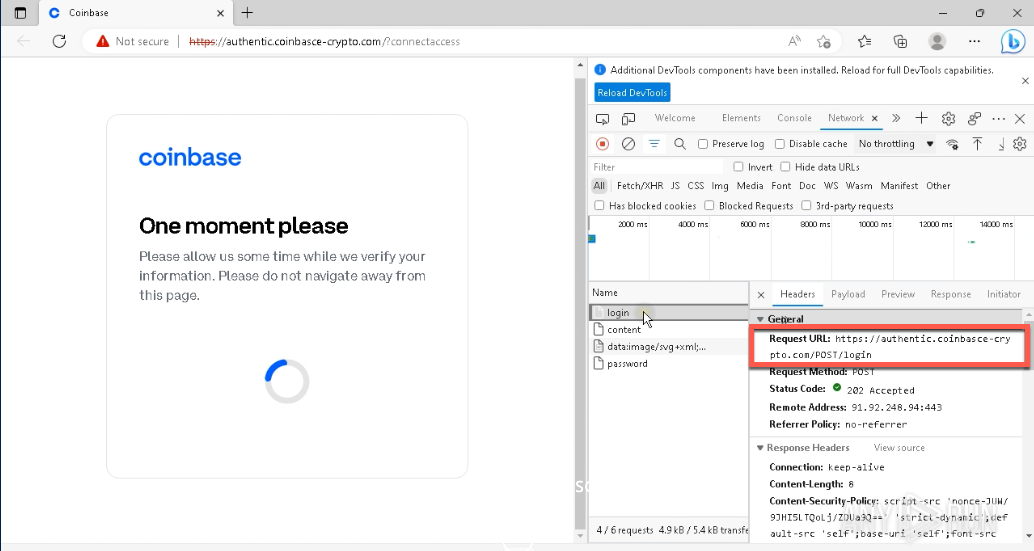
In the event that an individual enters their email address and password into the cloned (fake) Coinbase login page, an HTTP POST request is immediately transmitted to the attacker's command-and-control (C2) server. This allows the attackers to gain unauthorized access to the victim's Coinbase account, enabling them to obtain the victim's usernames and passwords. The attackers can then exploit this information to withdraw cryptocurrency from the victim's account, causing financial loss and potential harm to the victim. To prevent such attacks, it is important to be cautious and verify the authenticity of any login page before entering login credentials.
Figure 8 - HTTPS POST request is sent to the attacker C2 server
If we analyze this traffic with Wireshark (A network traffic analyzer), we can see that the web traffic is encrypted (we can’t see the all the data). However, we can see that our Chrome Web Browser is communicating with this malicious Coinbase cloned site by looking at the Server Name of the TLS Client Hello packet.
Figure 9 - HTTPS/TLS connection to coinbasce-crypto[.]com
How to Protect Your Crypto Accounts and Wallets!
In conclusion, the rising prevalence of cryptocurrency scams and crypto hacking incidents, as highlighted by the staggering $2 billion loss reported in 2023, demands increased vigilance from all users who interact with cryptocurrency, NFTs, and the Web3 landscape. The complex methods employed by sophisticated threat actors, such as those behind phishing attacks, pose a significant risk to individual crypto accounts, large and small.
Understanding the tactics utilized by scammers is crucial for safeguarding your cryptocurrency holdings. Phishing attacks, in particular, exploit psychological triggers through well-crafted emails, often impersonating reputable cryptocurrency platforms like Coinbase, Binance, and Exodus Wallet. These emails lead users to malicious documents or cloned websites, aiming to extract sensitive information, including usernames and passwords.
Please keep the following measures in mind to protect your cryptocurrency wallet and avoid falling victim to scams:
Enable Two-Factor Authentication (2FA): Two-Factor Authentication adds an extra layer of security to your crypto accounts, making it more difficult for attackers to gain unauthorized access.
Verify Email Authenticity: Be wary of unsolicited emails, especially those that demand urgent action, such as locking or freezing of your account. Verify the sender's email address and avoid clicking links or downloading attachments from unknown sources.
Check Website URLs: Before entering any login credentials, carefully examine the website's URL. Confirm that it is a legitimate platform by comparing it to official URLs and checking the presence of SSL/TLS certificates.
Educate Yourself: Stay informed about the latest phishing techniques and tactics used by scammers. Awareness is a powerful tool in preventing falling prey to deceptive schemes.
Regularly Update Security Software: Keep your antivirus and anti-malware software up to date to protect against new and evolving threats.
Exercise Caution with Email Attachments: Avoid opening email attachments from unknown sources, particularly if the email urges immediate action or seems suspicious.
By adopting these practices and staying informed, you can significantly reduce the risk of falling prey to cryptocurrency scams and enhance the security of your digital assets. In the ever-evolving landscape of cyber threats, proactive measures and a cautious approach are paramount to safeguarding your cryptocurrency wallet.
If you receive any suspicious emails feel free to reach out on social media and I will analyze them for you :)