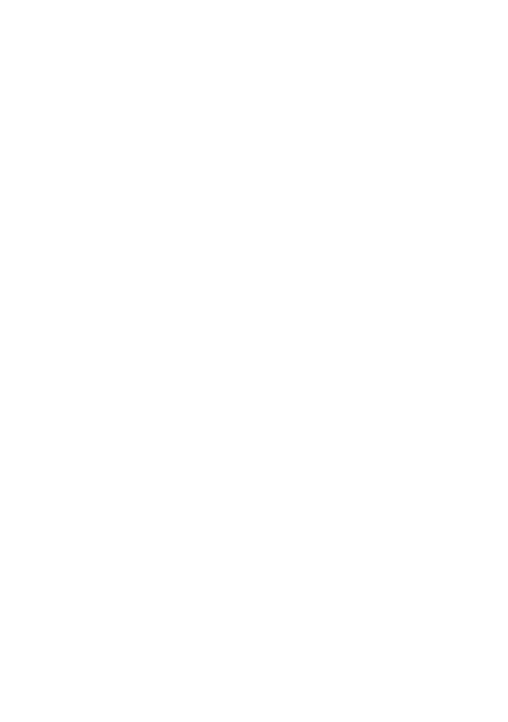Wireshark: Filter HTTP GET & POST Request Packets
Wireshark is a robust network protocol and packet analyzer that provides valuable insights into network traffic across each layer of the OSI model and the data transmitted between computers. Proficiency in filtering and analyzing Hypertext Transfer Protocol (HTTP) requests is critical for network administrators, engineers, and cybersecurity professionals. This blog post will explore Wireshark and examine how to utilize display filters to focus exclusively on GET and POST packets in layer 7 HTTP traffic. By doing so, we can better understand HTTP traffic and identify potential security and network issues.
Understanding Wireshark Display Filters
Wireshark allows network analysts to include display filters that allow network and security professionals to filter for specific types of network traffic. As networks tend to be very noisy, display filters make it easier to analyze and troubleshoot. Filtering GET and POST requests in HTTP traffic provides a targeted view of the required packets on the Application Layer (Layer 7 of the OSI model).
Figure 1 - Wireshark Display Filter Bar
Wireshark Display Filter: HTTP GET Requests
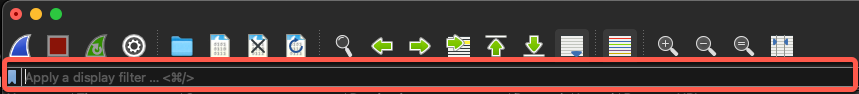
In Wireshark, GET requests can be isolated using the following Wireshark display filter:
http.request.method == "GET"
Figure 2 - Wireshark display filter for HTTP GET Requests
This filter narrows down the captured packets to display only those related to GET requests, enabling users to focus on the specific data transfers initiated by the GET method.
Wireshark Display Filter: HTTP POST Requests
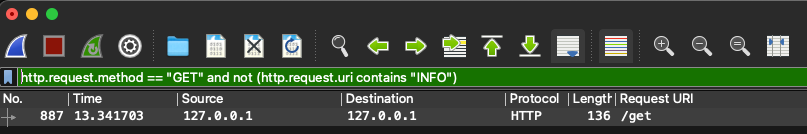
Similarly, POST requests can be examined by utilizing the following Wireshark display filter:
http.request.method == "POST"
Figure 3 - Wireshark display filter for HTTP POST Requests
This filter isolates packets associated with POST requests, facilitating the analysis of data exchanged during form submissions, file uploads, and other POST-related activities.
Combining GET & POST Wireshark Display Filters
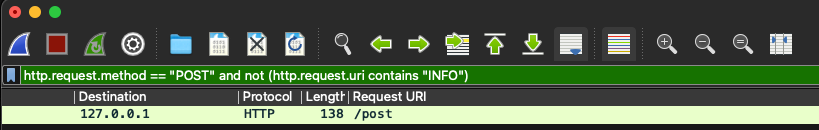
To obtain a more comprehensive view, Wireshark display filters can be combined to capture both GET and POST requests simultaneously using the Wireshark display filter logical operations “ or (||) “ operator:
http.request.method == "GET" or http.request.method == "POST"
Figure 4 - Wireshark display filter for HTTP GET & POST Requests
This filter allows users to monitor HTTP GET and POST requests, providing a holistic perspective on the network traffic associated with their web applications.
Practical Applications for Wireshark Display Filters
Using display filters in Wireshark to filter network traffic on packets containing HTTP requests such as GET and POST packets facilitates the identification of potential issues in web applications and web servers such as:
Slow-Loading Pages
Network Bottlenecks
Failed Form Submissions
HTTP Header Issues
Authentication Issues
Web Security Issues in Web Applications & Application Programming Interfaces (APIs)
Using filtered network traffic, a networking or cybersecurity professional can help troubleshoot and identify root causes in web applications.
Analyzing GET and POST requests is critical for security professionals. Unusual patterns or unexpected data in these requests could indicate malicious activity, making detecting and responding to potential threats easier. This analysis can be invaluable when creating patterns and detection guidance against exploits that exploit vulnerabilities in web applications and Application Programming Interfaces (APIs).
Analyzing specific types of HTTP requests can help users examine the efficiency of their web applications. From a network performance standpoint, these insights can be valuable for optimizing performance and enhancing the user experience.
Conclusion
Wireshark is a helpful tool for network and security professionals. It can help them understand and analyze network traffic. Wireshark is particularly good at isolating network traffic and can filter network traffic such as GET and POST requests within HTTP traffic using display filters. Professionals can better understand data transfers initiated by GET and POST methods by focusing on specific OSI model layers. This can help them troubleshoot problems with web applications.
The display filters in Wireshark are useful beyond just analyzing data. Network and cybersecurity professionals can use these filters to find potential problems in web applications and servers quickly. These filters can help identify slow-loading pages, failed form submissions, and security vulnerabilities. They can also detect unusual patterns in data and help identify potential threats.
Analyzing specific HTTP requests is also important for optimizing web application and network performance. This can help improve the overall user experience. Wireshark's display filters can provide valuable insights into optimizing performance.
Wireshark can empower network and security professionals to extract meaningful intelligence from network traffic. This can help them troubleshoot and improve their networks.
If you have any questions on how to use Wireshark display filters feel free to reach out on social media!